Public Key Infrastructure (PKI) #
PKI is a framework that involves processes, technologies, and policies to manage and secure digital communication. It issues digital certificates to authenticate the identity of users, devices, or services.
PKI is based on cryptography and encryption techniques and uses a pair of keys, a public key and a private key, to ensure security.
PKI in the automotive industry for diagnostic tool communication #
The PKI SaaS solution was introduced in the automotive industry to enable secure communication between the diagnostic tool and the ECU, such as during flashing, parameterizing, and replacing components.
SCALAR PKI Software as a Service (SaaS) #
The SCALAR PKI SaaS solution focuses on communication between the diagnostic tool through Authenticated Diagnostic Service (ADS) and ECU to ensure secure authentication.
The SCALAR PKI SaaS service offerings include issuing certificates for the client and server, along with the private and public keys, to uniquely identify individual users and electronic systems.
Unified Diagnostic Services (UDS) and Service 29 #
As modern vehicles have more intricate electrical systems controlled by ECUs and are getting interconnected, robust security mechanisms are required. The UDS protocol that incorporates security service 29 has been introduced to address evolving security needs.
It provides a mechanism to authenticate the client, such as a diagnostic tool, before providing access to specific data and diagnostic services within an ECU. The objective is to enhance security, prevent unauthorized access, and maintain the integrity of vehicle functions as per ISO14229.
This topic provides steps to perform the following core functions:
Request access to PKI certificate
Request management
Generate certificate
Request access to PKI certificate #
This feature enables various users of the organization to request certificate access for their respective use cases from the PKI module.
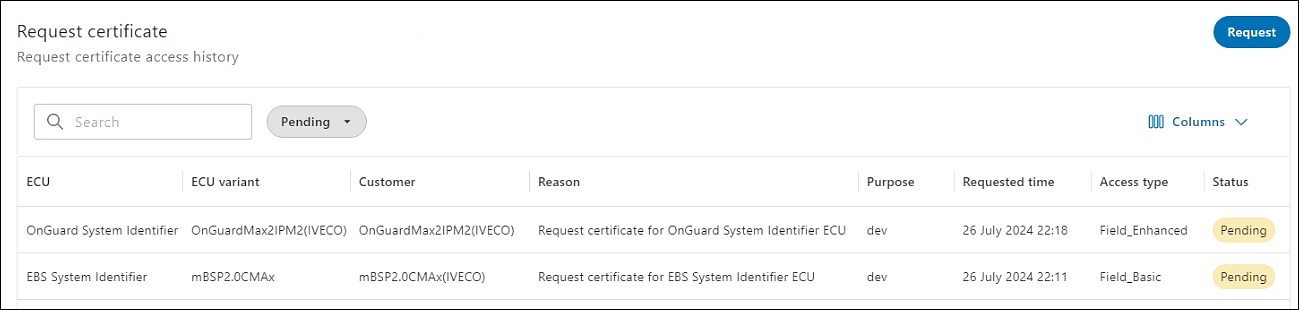
- In the PKI module > click Request access. The Request certificate page is displayed where all the requests and their status are listed.
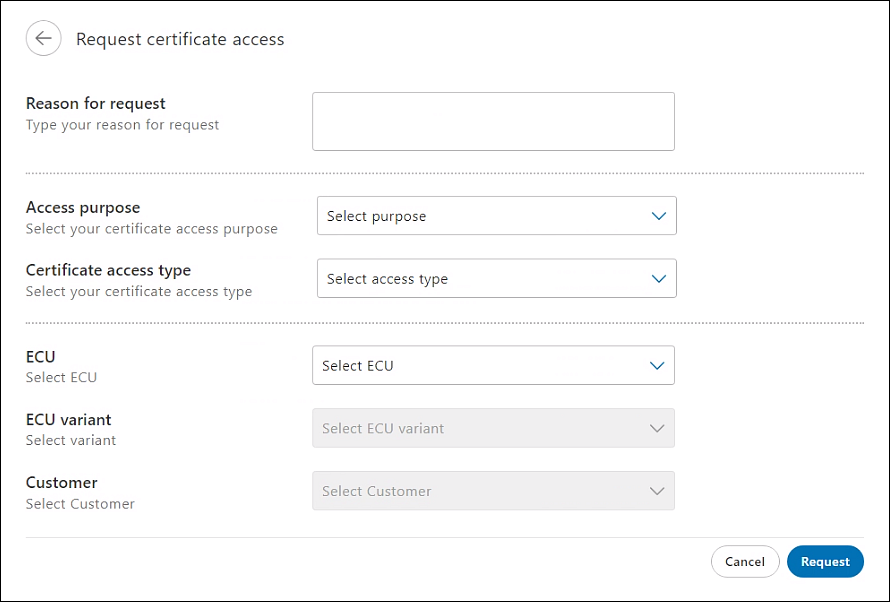
- On the Request certificate page, click Request. The Request certificate access page is displayed.
- Enter details in the various fields as explained in this table.
Field Action Reason for request Enter the purpose for creating this request.
Note: Explain the objective of requesting access to the ECU certificate policy.Access purpose Select the purpose to access the certificate.
Note: This field specifies why the user is requesting this certificate (for example, ‘Prototype Development’ or ‘Series’). If ‘Prototype Development’ is selected, the trust grade is applied at the development level. If ‘Series’ is selected, the trust grade is applied at the production level.Certificate access type Select the certificate access type.
Note: The type of certificate access defines the specific purpose and the certificate validity.ECU Select the ECU for which the certificate policy access is requested.
Note: All the available ECU policies for this organization are listed.ECU variant Select the ECU variant for which the certificate policy access is requested.
Note: All the available ECU variants for the selected ECU are listed. If a variant is not available for this ECU, you will not be able to select any option. - On the Request certificate access page, click Request. The Request certificate page is displayed.
Note: An email notification is sent to the PKI administrator for approval. After approval, you can generate the certificate in the Generate certificate page.
Request management #
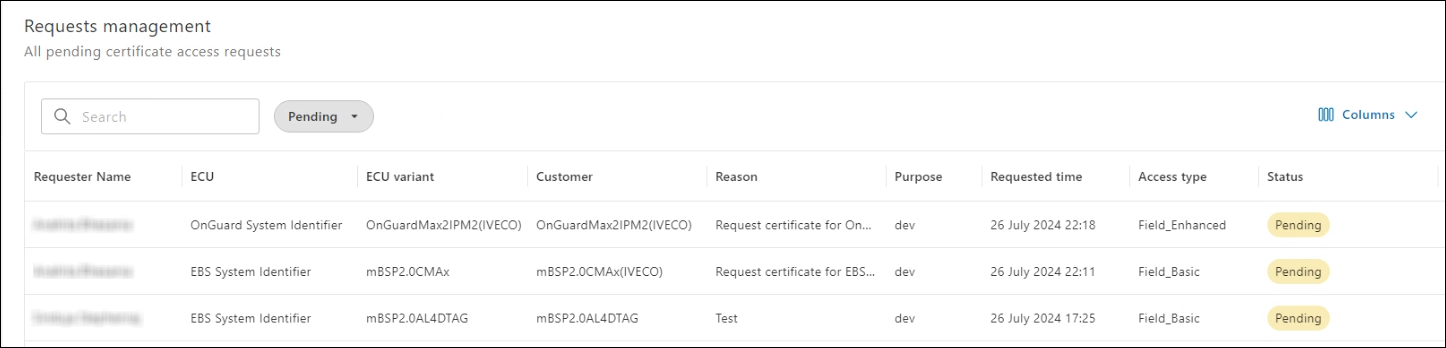
The PKI administrator can view all the requests along with the status. The administrator can approve or reject the request.
- In the PKI module > click Request management. The Request management page is displayed.
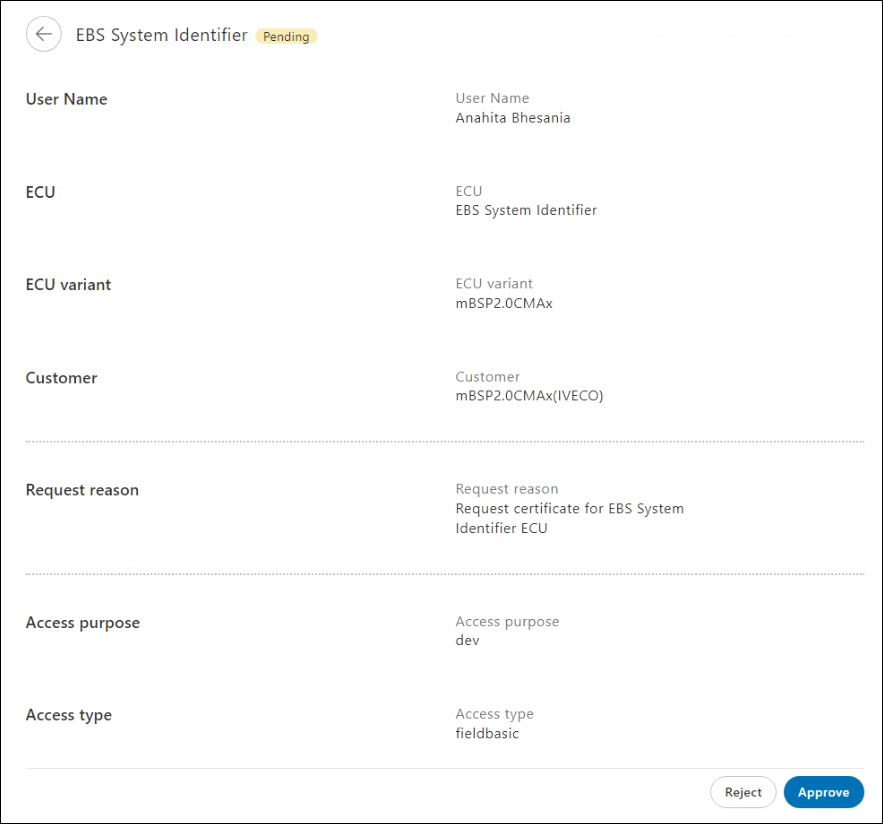
- To review the requested ECU certificate policy details, click the required record. The page containing the reason for the request and the ECU certificate policy details is displayed.
- Do one of the following:
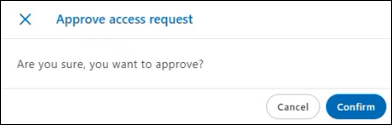
- Click Approve. The Approve access request dialog is displayed. To approve the request, click Confirm.
The request is approved. After the request is approved, the certificate requestor can generate a certificate and download it from the Generate certificate feature.
Note: An email notification is sent to the certificate requester.
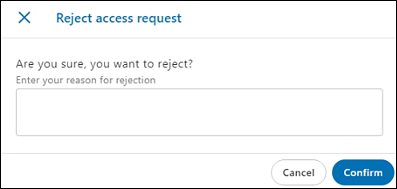
OR - Click Reject. The Reject access request dialog is displayed. To reject the request, enter the reason for rejection, and then click Confirm.
The request is rejected.
Note: An email notification is sent to the certificate requester.
- Click Approve. The Approve access request dialog is displayed. To approve the request, click Confirm.
Generate certificate #
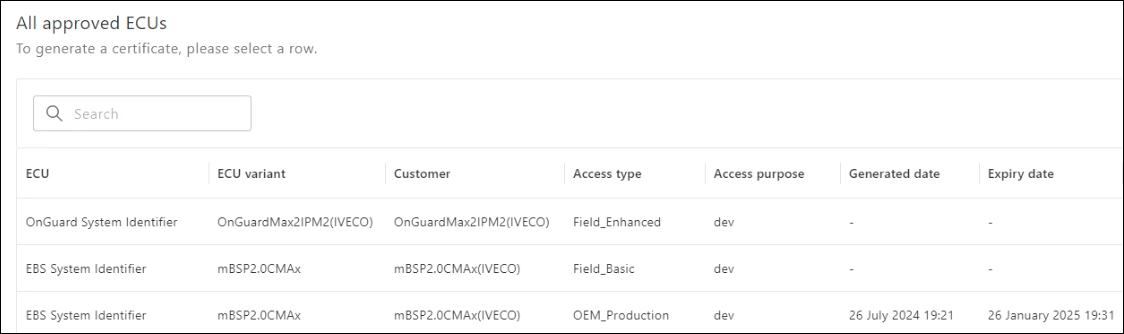
All the certificate policies to which the user has access are listed on the All approved ECUs page. You can generate and download the certificates and the key pair.
- In the PKI module > click Certificates. The All approved ECUs page is displayed.
Note: The ECU certificate policies that are approved are listed. - To generate a certificate, select the required record. The page containing ECU certificate policy details is displayed.
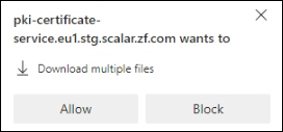
- Click Generate. The dialog to download the files is displayed.
Note: After a certificate has been generated, you can click Download to regenerate the certificate. - On the dialog to download the files, click Allow.
The following files are downloaded: the private key file and the certificate file. Both the files are DER encoded and saved as Privacy Enhanced Mail (PEM) type.
Note:
- As a key pair, the public and private keys work in combination. The private key is not stored on the server for security reasons.
- You must save the private key after generating the certificate. For security reasons, maintain confidentiality of the private key.
- Any user who has access to the private key can also access the ECUs linked to those keys.
- The certificate can be downloaded multiple times until the expiration date.
- In the event that the key is lost, click Generate to generate the certificate again even if the expiration date is not reached.